Gecko Security
AI-powered security engineer that detects and fixes business logic and multi-step vulnerabilities with low false positives.
At a Glance
Pricing
Get started with Gecko Security at no cost with Scan 1 public open-source repository and Basic vulnerability detection.
Engagement
Available On
Updated Feb 2026
About Gecko Security
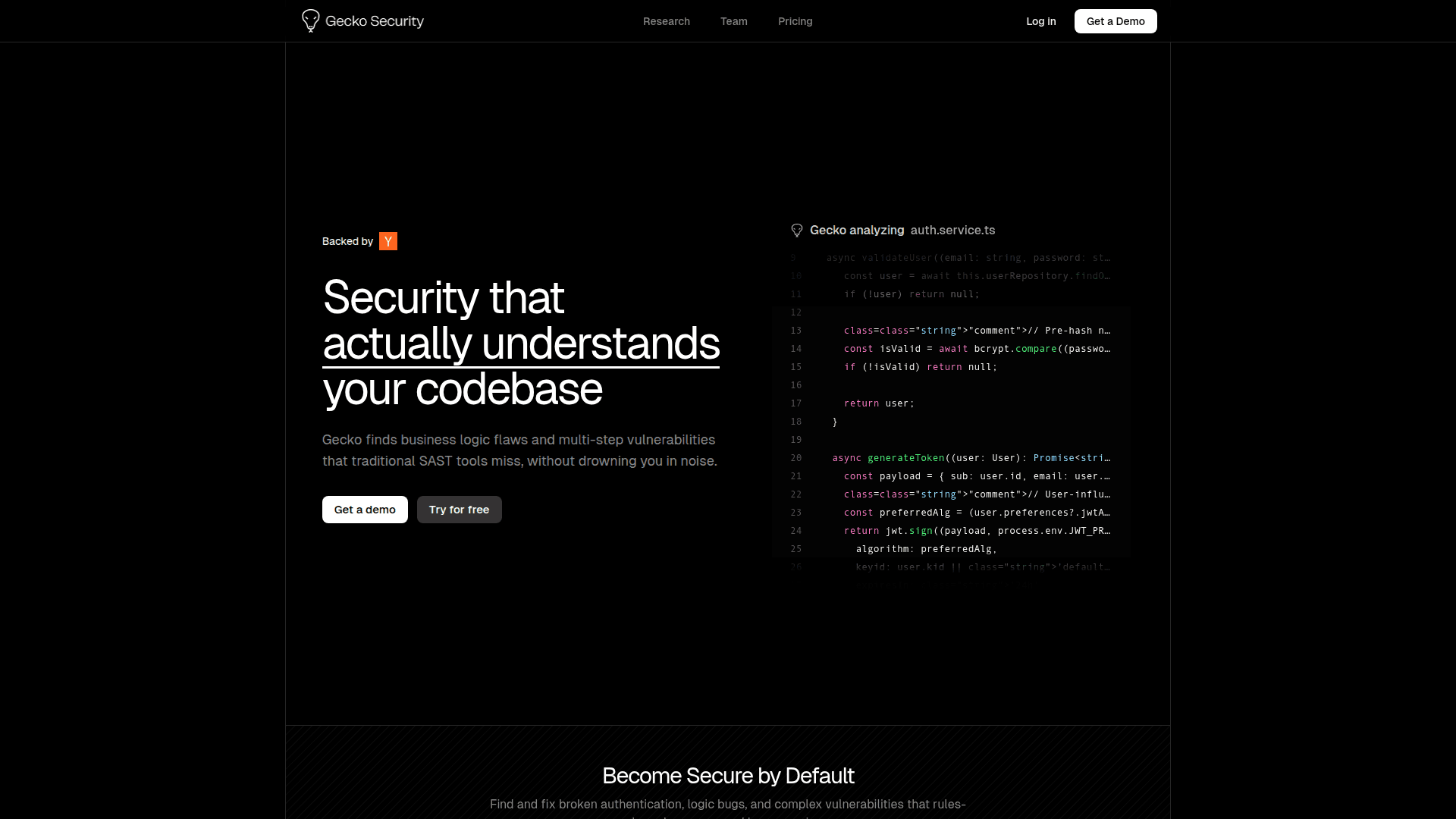
Gecko Security is an AI-driven security platform designed to detect and remediate vulnerabilities that traditional SAST tools often miss. Instead of relying solely on abstract syntax trees, Gecko builds a semantic understanding of your codebase to uncover business logic flaws and multi-step vulnerabilities. The system validates exploits, models threats, and generates actionable proof-of-concepts with suggested fixes. Gecko integrates with CI/CD workflows, provides a PR bot for real-time feedback, and supports SOC 2 compliant private/self-hosted deployments for enterprises. Founded in 2024 and backed by Y Combinator, Gecko is built by a team with backgrounds in intelligence, Interpol, and applied AI research.
Community Discussions
Be the first to start a conversation about Gecko Security
Share your experience with Gecko Security, ask questions, or help others learn from your insights.
Pricing
Free Plan Available
Get started with Gecko Security at no cost with Scan 1 public open-source repository and Basic vulnerability detection.
- Scan 1 public open-source repository
- Basic vulnerability detection
- Automated remediation suggestions
Pro
Professional plan with Up to 30 repository scans (public and private) and Advanced vulnerability detection with proofs-of-concept for power users.
- Up to 30 repository scans (public and private)
- Advanced vulnerability detection with proofs-of-concept
- Team support for up to 5 developers
- CI/CD integration and PR bot
- Prioritized security findings
Enterprise
Enterprise-grade solution with Unlimited repositories and Custom vulnerability rules and dedicated support.
- Unlimited repositories
- Custom vulnerability rules
- Automated threat modeling and exploit validation
- API access and custom integrations
- Single Sign-On (SSO) and Role-Based Access Control (RBAC)
- Audit logs and compliance features
- Private/self-hosted deployment options
- Line-level code fix suggestions
Capabilities
Key Features
- Semantic AI code analysis for business logic flaws and multi-step vulnerabilities
- Threat modeling with simulated attack paths and exploit validation
- Proof-of-concept generation and AI-driven code fixes
- CI/CD integration with PR bot for real-time vulnerability feedback
- Lower false positives (~20%) compared to traditional SAST tools
- SOC 2 compliance and private/self-hosted deployment support
- Supports both public and private repositories
- Automated code remediation suggestions
Integrations
Demo Video